
First, some facts. Of the Computer and Information Systems Security graduates we've analyzed , here's how many have used (or NOT used) their degree in their career:
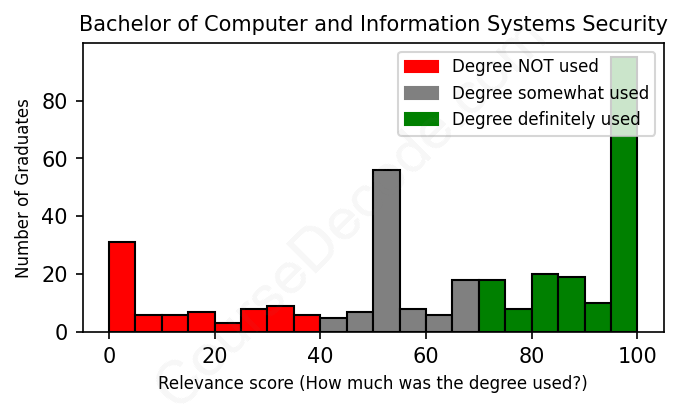
These are estimates based on AI analysis of 346 LinkedIn profiles (see below).
The verdict? Slightly below average. Overall, with an average relevance score of 63%, Computer and Information Systems Security graduates have a slightly lower likelihood (-4%) of finding work in this field compared to the average graduate across all fields:
And for comparison, here's the chart for all profiles we've looked at across all degrees.
Also, after graduating, only 17% of these graduates have pursued further education other than another Bachelor's degree (such as a Masters degree or other), compared to the average across all profiles of 35%. This suggests a Bachelors degree is enough for most Computer and Information Systems Security graduates, and it's normal to look for work straight after graduation.
See the details:
|
Relevance score: 0% We think this person has NOT gone into a career related to their degree. We think this person has NOT gone into a career related to their degree.
DEGREE INFOGraduated in 2023 from Tarleton State University with a Bachelor's in Computer Information System in Computer and Information Systems Security. No other secondary education since. JOB HISTORY SINCE GRADUATIONSales Associate ABC Smoke Shop Feb 2023 - Present ABOUTNo information provided. |
The top 10 most common jobs done by the graduates we've analyzed (ranked most common to least) are:
When analyzing the career paths of individuals who graduated with a degree in Computer and Information Systems Security, we see a broad spectrum of job titles and roles that reflect varying relevance to their field of study. While many have successfully transitioned into roles that directly apply their security knowledge and skills, others have found themselves in positions that only loosely connect to their academic background. It's intriguing to observe which specific job types dominate and how well they correspond to the core principles of information systems security.
From the data gathered, one of the most common job types represented is IT Support or Technical Support roles. Positions like Help Desk Technician, IT Specialist, and Support Analyst are frequently noted. While these roles do require some understanding of information systems, they often focus more on troubleshooting and customer service rather than the security principles emphasized in their degree. Consequently, many individuals in these roles may not be leveraging their security expertise in a significant way on a daily basis.
Moving up the spectrum, we also see a noticeable presence of roles that are more aligned with information security, such as Cybersecurity Analyst, Security Consultant, and System Administrator. These job titles demand the direct application of security knowledge and practices and are linked closely to the studies undertaken in Computer and Information Systems Security programs. For instance, roles that specifically mention security responsibilities tend to correlate well with educational goals, showing that those pursuing careers directly related to security tend to find relevant positions after graduation.
Furthermore, positions such as Project Managers or System Engineers often require candidates to have a solid understanding of both project management principles and security measures, reflecting a more integrated approach. These individuals often manage teams working on information security, thus applying their degree knowledge in strategic, managerial roles rather than just technical tasks. It's also worth noting the engineering positions related to development and network security where skills learned in their degree program are integral to the job—but may not necessarily be labeled as "security" roles.
However, a significant number of graduates have taken up jobs that diverge considerably from their field of study. For instance, roles within marketing, human resources, and operations management appear throughout, showcasing individuals who may not directly apply their computer and information systems security knowledge. These individuals might utilize skills like analytical thinking or problem-solving but often in a context unrelated to information security protocols, which raises questions about the applicability of their training in the workforce.
In conclusion, it's clear that while many graduates from Computer and Information Systems Security programs secure positions related to their field, a notable percentage may find themselves in roles that do not fully utilize their degree's core concepts. This disparity signals a potential gap between educational preparation and career application for some individuals. Those aiming for the most relevant positions may benefit from pursuing internships and work experiences during their studies that align closely with cybersecurity roles to ensure a smoother transition into the workforce post-graduation.
Here is a visual representation of the most common words in job titles for Computer and Information Systems Security graduates:
Looking at the career trajectories of graduates in Computer and Information Systems Security, it’s quite interesting to observe how their paths unfold over time. For many of these individuals, their first jobs after graduation tend to be in technical roles such as helpdesk support, IT support technician positions, or junior analyst roles. It makes sense since these positions often serve as stepping stones into the more specialized areas within computer and information security. A good number of grads are taking initial steps like being IT support specialists, system administrators, or helpdesk technicians, giving them exposure to real-world IT environments and help them to build essential technical skills.
Fast forward five years, and we see a significant evolution in their careers. Many make the leap into more specialized areas, like cybersecurity analysts, security operations center (SOC) analysts, or IT project managers. This upward movement illustrates how critical initial experience is to carve out a niche in the ever-evolving tech landscape. By around ten years post-graduation, many alumni find themselves in senior or management roles, leading teams of specialists as IT security managers, solutions architects, or even in executive positions like chief information security officers (CISOs). The trend shows that a considerable number are indeed progressing into well-respected and lucrative careers centered around information security and technology leadership. This is definitely a testament to the value of education in this field, as many alumni leverage their foundational knowledge to secure significant roles within various companies.
However, like any field, there are also those whose careers seem to have drifted into roles that are not strictly related to Computer and Information Systems Security. For some graduates, the journey seems less linear, with individuals settling into various roles that may not completely utilize their degree. This could include positions in IT support that don’t lead toward security, marketing roles, or completely different career paths altogether. Though it’s not as common, it's an honest reality of the job market where the most direct path from education to career isn’t guaranteed for everyone. Nonetheless, the strong representation of professionals in high-level IT security jobs shows that many graduates successfully find their place in the booming cyber security sector. Overall, graduates from this discipline appear to have favorable career trajectories that, while sometimes meandering, ultimately lead to rewarding and relevant opportunities in the tech world.
Honestly, a Bachelor’s degree in Computer and Information Systems Security can be pretty challenging, but it's not impossible! If you’ve got a knack for tech and are willing to put in the effort, it can be manageable. You'll dive into subjects like networking, cryptography, and cybersecurity principles, which can get pretty deep, especially if math isn't your strongest suit. Some folks find the hands-on labs and projects super engaging, while others might struggle with the more theoretical stuff. Overall, I'd say it’s about average for a degree—definitely requires dedication and a willingness to learn, but if you're motivated, you can definitely pull it off!
Most commonly, in the LinkedIn profiles we've looked at, it takes people 4 years to finish a Bachelor degree in Computer and Information Systems Security.
When looking at the job trajectories of these Computer and Information Systems Security graduates, it's clear that many have landed some pretty decent positions right after graduation or have progressed significantly in their careers. For example, graduates from schools like Georgia State University, University of Houston, and Arizona State University have moved into roles at larger companies like Amazon Web Services and Deloitte, which typically offer competitive salaries. However, not every graduate has hit the jackpot—some found themselves in more entry-level positions or roles that may not pay as well, like tech support or operations roles, especially if they graduated from institutions that aren't as recognized in the industry.
Overall, while there are definitely some graduates who are making solid money, particularly those who quickly climbed the ranks in tech companies or landed roles in cybersecurity, there are also plenty who are still working their way up and might be on the lower end of the salary spectrum. As with many fields, it seems that one’s university, the job's industry, and individual career choices can all significantly influence earning potential. So, if you’re looking at this field, aim for the top schools and internships to help kick-start your career on the right foot!
Here is a visual representation of the most common words seen in the "about" section of LinkedIn profiles who have a Bachelor degree in Computer and Information Systems Security. This may or may not be useful:

Here are all colleges offering a Bachelor degree in Computer and Information Systems Security (ordered by the average relevance score of their Computer and Information Systems Security graduates, best to worst) where we have analyzed at least 10 of their graduates:
| College | Score | Count |
|---|---|---|
 University of Houston University of Houston
|
76 | 11 |
 California State Polytechnic University-Pomona California State Polytechnic University-Pomona
|
62 | 14 |
 University of Phoenix University of Phoenix
|
52 | 13 |